Small Wireless Networks and their Vulnerabilities
Wireless networking quickly has been adopted by homes and business after its introduction. These 802.11x networks have provided cable free access to privately owned networks and the Internet. This form of networking is extremely cost-effective and easy to set up for the not-so-technical individual. Both home and small business network access points are easily found in any major department store for usually less than $100. Higher end models such as those developed from Cisco come with many more features for the networking engineer wishing to implement them into a project. However, along with these features comes a much higher price. This paper mainly focuses on non-professionally installed Wireless networks.
“The potential presence of 10 billion such devices over the next decade [introduces serious questions of security.] ” (Osorio, 2008, p. 92) New security protocols have been developed to protect the traffic of a network as well as maintain access only to those authorized. These protocols have displayed both vulnerability and security when implemented into wireless networks. Another major issue in the security of wireless networks is the human factor. Often lack of technical knowledge or ignorance to potential threats plays a role in the nonexistent or poor network security measure employed.
Legal Cases of Wireless Network Intrusion
Protection against network intrusion in a home and business environment is a necessary step to avoid potential personal loss of digital property, direct monitoring of activity and network abuse by those connecting without permission (US-CERT, 2006). Most unsecure networks will simply be used for leaching Internet and other harmless activities. However, a malicious user successfully connected to a unsecure wireless access point could utilize this connection to further carry out attacks anonymously under the cover of the parent network.
In 2004, a California man was arrested for the malicious intrusion of several unsecured networks to send commercial adult electronic email advertisements. Nicholas Tombros of Hollywood, California used email addresses he obtained from a previous employer to orchestrate his mass spam attack. Even though Tombros was Operating under the cover of other people’s networks he was eventually traced back due to his affiliation with the site he promoted. (Slay & Turnbull, 2005)
Another case of malicious intent involved two men named Adam Botbyl and Brian Salcedo in 2004 who utilized a unsecured access point to infiltrate Lowes corporate data center. The two men were convicted of accessing consumer credit information from the Lowes home improvement store chain and sentences to several years in a federal correctional facility. (Sipior & Ward, 2007) These men utilized a network weakness which, not only caused potential monetary loss, but also affected the reputation of the company.
Wireless Network Security Protocols
Wireless network security protocols were designed to provide a way for the owner of a wireless access point to ensure that the use of the network is theirs or those they permit only. To avoid unauthorized users from maliciously using a wireless network it is necessary to utilize at least one of the network security protocols below. Although there has been research conducted to compromise these security protocols utilizing any of them is better than no security at all.
Below are the basic features of each of the popular protocols found on most of today’s wireless access points.
| Security Protocol | Acronym | How it works |
| Wired Equivalent Privacy | WEP | Uses less advanced algorithms that can be decrypted using tools available on the Internet. |
| Wi-Fi Protected Access | WPA | Contains many security improvements over WEP. Utilizes key hierarchy that protects the existence of the WPA main Key. |
| Wi-Fi Protected Access 2 | WPA2 | Contains all WPA features plus Advanced Encryption Standard (AES). This new encryption standard is far more advanced than previously used RC4 encryption. |
Security Risks and Benefits of Network Monitoring Tools
Modern home and small business routers and commercial access points could utilize the security protocols discussed in the previous section. Although these routers and access points provide the option to employ security measures often these measures are dismissed by the people installing the hardware. The human factor or wetware aspect of this installation process provide an abundance of security risks to the owner(s) of the hardware and network.
Wireless networks are easily able to be detected utilizing network monitoring tools freely available on the Internet. These network tools come in either the form of simple point and click or full powerful command-line-driven software packages. Combined with the necessary network card that allows monitor (promiscuous) mode any person with a laptop can perform a War Driving session (described in the next section).
Although these tools appear to be made with hostile intent, and if used for such can provide serious network risk, they are often used for honest network monitoring applications and vulnerability assessments. “The difference between wireless hacking and wireless monitoring is intent and moral orientation” (Berghel, 2004, p. 25). Utilizing these tools for network discovery purposes have several benefits for those wishing to increase network performance as well as assessing their own network vulnerability. These benefits include the ability to view other local access points channels to make the necessary adjustments to avoid channel overlapping to increase network performance. Another key benefit is to see what networks are freely broadcasting their Service Set Identifier (SSID) and the type of encryption being used. This information can be valuable to a network administrator or a home user wishing to secure his or her network(s) from possible intrusion.
War Driving
In 1983 the movie WarGames starring Matthew Broderick as David, a young boy who had a love for video games utilized a program to dial up all the numbers in his home town of Sunnydale, California in search of a open modem connection. During the execution of David’s war dialing program he happened to stumble across a NORAD open line that connects him to a super-computer that controls the nuclear arsenal of the United States government. Although this was just a movie the applications of war dialing as a viable way to find open connections to networks have been proven throughout the years. Evolution of wireless technology has created a much easier and faster way of being able to discover open network connections that more than often lead to a gateway to the internet.
Today’s world of wireless access points both in home and business have led to a new form of war dialing to emerge called War Driving. Although different in technical aspects the concept of this form of network discovery remains. Similar to War Dialing that capitalizes on dial up network connections, War Driving capitalizes on those networks connected to a wireless access point.
Exploitation of Network Vulnerabilities
In this section of the paper the focus of network vulnerabilities of wireless networks is met with research using several tools to provide a clear understanding of the network security flaws found in a majority of access points monitored. The penetration test was on a wireless router using WEP protocol security was performed in a home test environment with the consent of the owner. As a preface to this test a War Driving session was performed with a network monitoring program. This program in no way attempted to connect to any networks to gain unauthorized access. This War Driving session had the sole intention to collect information on the network security used.
Results of War Driving Test
The test utilized a netbook with the Ubuntu 11.04 operating system installed running the Aircrack-ng (www.aircrack-ng.org) monitoring function Airodump-ng. The hardware utilized with the netbook was a Linksys Compact Wireless-G USB adapter that was purchased from Ebay for $13. Airodump-ng was set to write an output in the form of a CSV file in order to further analyze the results.
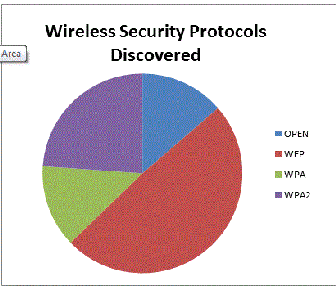 Figure 1, Wireless Security Protocols Analyzied during the War Driving session Figure 1, Wireless Security Protocols Analyzied during the War Driving session |
The location of this test was a radius of two miles that was selected do to the population of apartment buildings and the high likely hood of creating a larger sample size. A total of 352 total access points were recorded during a 45 minute run. Airodump-ng was configured to monitor all Wi-Fi channels in order not to focus on one specific popular channel. This approach led to a broader range of access points of both business and home hardware that may have been over looked during the process. Although other protocols than WEP, WPA, and WPA2 exist only these security protocols were assessed in the War Driving session.
The results of the War Driving session were unquestionably stunning. Of the 352 total access points monitored 48 were unsecured completely. (Figure 1) This represents approximately 14% of the overall access points assessed. The total amount of unsecured known business Wi-Fi connections collected during this session neared 21% of those 48 monitored.1
1Due to the scope of this test it is unclear how many of this 21% are vulnerable to attacks as very few may be unsecured Wi-Fi for public use and may not be connected to a valuable computing network source.
Wired Equivalent Privacy (WEP) was the next concern of this War Driving Session. During the 45 minute run an inexcusable 49% of all access points still used the WEP security protocol for security against outside attacks. Of these access points only 1% were businesses. Ironically that 1% consists of a local computer company that deals in Point of Service systems specializing in RFID and wireless tracking technology.
Wi-Fi Protected Access (WPA) and Wi-Fi Protected Access 2 (WPA2) comprised of 37% of overall network security protocols utilized in the War Driving session. Broken down WPA was 17% and WPA2 24%. Although these network protocols are able to be compromised, the amount of time and effort to do so negates the risk. It is plausible that a brute force attack could be utilized to gain access to this type of Wi-Fi connection however availability of other networks with little to no security would surely steer those with malicious ambitions away. Unless the intent is to attack such a network this security protocol is found as being the safest and most secure way of managing a wireless network.
Results of Penetration Test on WEP Network
The statistics in (Figure 1) have displayed that not only is 14% of the access points were readily available for an attack but 49% of the access points assessed were utilizing poor security or WEP. Known vulnerabilities have rendered WEP useless in the wireless protection realm. These vulnerabilities have rendered 63% of all networks surveyed as potential targets for malicious attacks or intrusion. Below the steps to crack a 64 bit web password are briefly discussed. The results are displayed in figure 2.
For this test a desktop computer running a virtual machine with Backtrack 5 Linux distribution (www.backtrack-linux.org) loaded is using the Linksys Compact Wireless-G USB adapter in monitor mode. Backtrack 5 comes pre-installed with many useful penetration testing software packages however, for this test the focus is on Aircrack-ng (www.aircrack-ng.org). Below is a summary of the necessary steps used in this type of attack. Notice that no command line functions are given however they can be easily found on the Internet with a simple search. (see Singh et al, 2010, for further information)
1. If this were a malicious attack the attacker would change their MAC address using a tool, included in Backtrack Studio 5, called MACCHANGER. Because this was in a test environment this step was skipped.
2. This step is the discovery phase that requires using the airmon-ng tool to discover MAC address of access points within range. Other useful information is given such as the ESSID, speed, encryption, and channel.
3. Once the targets necessary information is collected, it is necessary to monitor the packets coming from and to the access point. This is done using airodump-ng which allows the attacker to capture and record activity into a file, which will then be used by the aircrack-ng program.
4. Since all packet information is being collected it’s time to speed up the process using a aireplay-ng. This creates network traffic which speeds up the packet collection process.
5. Finally the file created to collect packets is piped into aircrack-ng. This software examines the collected packets and decrypts the WEP key
After successfully doing this crack 4 consecutive times the average time was approximately 14 minutes. If an attacker had the intent to break into this type of network they could achieve with speed and accuracy using the tools mentioned above. This test shows how vulnerable a wireless network is that uses poor security.
Summary
Wireless technologies will continue to grow due to its ease-of-use and cost-effective implementation. “The public is becoming accustomed to the mobility and ubiquitous internet access they provide” (Chenoweth et al., 2010, p. 134). As time goes by new security measures and protocols will be created and installed in wireless access points. Although these new security precautions will be available it is the responsibility of the human factor to implement them. The War Driving test in the previous section displayed that not only were more advanced security options not being used, but often no security at all was in place. General home and small office Wi-Fi network owner need to be educated in the uses of security on their access points.
References
Berghel, H. (2004). Wireless Infidelity I: War Driving. Communications of the ACM, 47(9), 21- 26..
Chenoweth, T., Minch, R., & Tabor, S. (2010). Wireless Insecurity: Examining User Security Behavior on Public Networks. Communications of the ACM, 53(2), 134-138.
Lashkari, A.H.; Danesh, M.M.S.; Samadi, B.(2009)A survey on wireless security protocols (WEP, WPA and WPA2/802.11i), Computer Science and Information Technology, 2009. ICCSIT 2009. 2nd IEEE International Conference, pp.48-52, doi:10.1109/ICCSIT.2009.5234856
Slay, J. J., & Turnbull, B. B. (2005). The 802.11 technology gap: case studies in crime. Retrieved from EBSCOhost.
Sipior, J. C., & Ward, B. T. (2007). Unintended Invitation: Organizational Wi-Fi use by external roaming users. Communications of the ACM, 50(8), 72-77.
Singh, A., Mishra, B., & Singh, S. (2010). WLAN Security Flaw: Cracking 64 bit WEP Key. International Journal of Computer Science Issues (IJCSI), 7(6), 296-299
United States Computer Emergency Response Team. (2006). Using Wireless Technology Securely. Retrieved June 19th, 2010, From http://www.us-cert.gov/reading_room/Wireless- Security.pdf