I was introduced to this amazing tool by Siemsen named Switchmap. It uses snmp, cdp and some wonderful magic to populate a SEARCHABLE index of all of your switches interfaces. It is any easy way to see what is attached to what interface and best of all yes I need to say it again it is searchable. For instance want to see what dell devices are on what interfaces on what switches… easy, search for it. Switchmap translates the OUI of a MAC address to the manufacturer. Definitely check it out my description simply doesn’t do it justice.
Junos Essentials Guide
Hey guys! I just wanted to share a guide I made when I was studying for the JNCIA-Junos exam. It is pretty basic and may have some errors here and there. Feel free to download away. I added a doc version incase you wish to add anything or personalize it for your own studies. Let me know if you add anything I’d love to see it!
Home ESX lab
I’m in the process of converting my once gaming desktop to an ESX server(build found below). I just bought an Intel PRO/1000 MT Dual Port Server Adapter since even though RealTek 8111e’s are supported in ESX 5 they simply do not pass traffic. It is a shame since there are 2 on-board gigabit nics in the motherboard. I have seen where people were able to get them working however after about 2 days of trying I’ve come to the realization that I should just buy and $18 dollar dual nic and move on. I did try to insert the drivers into the 4.1 release and go figure nothing.
I copied a lot of my build from http://tinkertry.com/vzilla/.
ASRock Z68 PROFESSIONAL GEN3 LGA 1155 Intel Z68 HDMI SATA 6Gb/s USB 3.0 ATX Intel Motherboard
Intel Core i7-2600 Sandy Bridge 3.4GHz (3.8GHz Turbo Boost)
Corsair Force Series GT CSSD-F120GBGT-BK 2.5″ 120GB SATA III Internal Solid State Drive (SSD)
G.SKILL Ripjaws X Series 32GB (4 x 8GB) 240-Pin DDR3 SDRAM DDR3 1333 (PC3 10666) Desktop Memory
If anyone has any ideas on storage please post below. I was thinking about an hp proliant microserver… who knows as of now…
Tacacs + AD + CentOS = FREE
So I recently had to set up a TACACS+ server connected to AD. I decided to go with CentOS 6 x64 as the OS of choice. I have to say it took a lot. Perhaps its because I’m not a Linux guy. Anyway below are all the steps I took to get it working. If you have any questions at all post away. Also make sure you check out https://groups.google.com/forum/?fromgroups#!forum/event-driven-servers if you have any extremely in depth questions. This group has a lot of great posts that really helped me out.
The following installs the TACACS+ server on a Centos 6 64 VM. It allows the ability to restrict access to groups of individuals according to their Active Directory membership. The current script setup uses the user domain credentials for both the username and password and the enable password.
NOTE: The user guide can be found at http://www.pro-bono-publico.de/projects/unpacked/doc/tac_plus.txt.
Install Dependencies
1. yum install gcc
2. yum install g++
3. yum install perl-IO-Socket-SSL
4. yum install pam-devel
5. yum install ld-linux.so.2
6. wget http://search.cpan.org/CPAN/authors/id/G/GB/GBARR/perl-ldap-0.39.tar.gz
7. tar –xzvf perl-ldap-0.39.tar.gz
8. cd perl-ldap-0.39
9. perl Makefile.PL // say yes to everything
10. perl -e “use IO::Socket::SSL”
11. perl -e “use Net::SSLeay”
12. cpan
a. > Install Net::LDAP // select yes to everything
13. Yum install perl-LDAP
Install Tac_Plus
1. wget http://www.pro-bono-publico.de/projects/src/DEVEL.tar.bz2
2. bzip2 -dc DEVEL.tar.bz2 | tar xvfp –
3. cd PROJECTS
4. su
5. ./configure
6. Make
7. Make install
Install tac_plus.cfg file
1. cd /usr/local/etc/
2. vi tac_plus.cfg
3. cp /usr/local/sbin/tac_plus /etc/init.d/
4. cd /etc/init.d/
5. ll | grep tac_plus //make sure that permissions are set -rwxr-xr-x
6. tac_plus /usr/local/etc/tac_plus.cfg //verify the config file
7. env LDAP_HOSTS=”<LDAP IP>” /usr/local/lib/mavis/mavis_tacplus_ldap.pl
//insert IP of LDAP server
8. vi resolve.conf
a. add this line to the file:
nameserver <ip of AD>
Add AD to hosts file to enable LDAPS
1. vi /etc/hosts
2. add <IP Address> <Full Domain Name>
Example:
127.0.0.1 localhost localhost.localdomain localhost4 localhost4.localdomain4
::1 localhost localhost.localdomain localhost6 localhost6.localdomain6
10.10.10.10. xxxxx.xxxx.local
3. wq
The following installs the TACACS+ server on a Centos 6 64 VM. It allows the ability to restrict access to groups of individuals according to their Active Directory membership. The current script setup uses the user domain credentials for both the username and password and the enable password.
NOTE: The user guide can be found at http://www.pro-bono-publico.de/projects/unpacked/doc/tac_plus.txt.
Install Dependencies
1. yum install gcc
2. yum install g++
3. yum install perl-IO-Socket-SSL
4. yum install pam-devel
5. yum install ld-linux.so.2
6. wget http://search.cpan.org/CPAN/authors/id/G/GB/GBARR/perl-ldap-0.39.tar.gz
7. tar –xzvf perl-ldap-0.39.tar.gz
8. cd perl-ldap-0.39
9. perl Makefile.PL // say yes to everything
10. perl -e “use IO::Socket::SSL”
11. perl -e “use Net::SSLeay”
12. cpan
a. > Install Net::LDAP // select yes to everything
13. Yum install perl-LDAP
Install Tac_Plus
1. wget http://www.pro-bono-publico.de/projects/src/DEVEL.tar.bz2
2. bzip2 -dc DEVEL.tar.bz2 | tar xvfp –
3. cd PROJECTS
4. su
5. ./configure
6. Make
7. Make install
Install tac_plus.cfg file
1. cd /usr/local/etc/
2. vi tac_plus.cfg
3. cp /usr/local/sbin/tac_plus /etc/init.d/
4. cd /etc/init.d/
5. ll | grep tac_plus //make sure that permissions are set -rwxr-xr-x
6. tac_plus /usr/local/etc/tac_plus.cfg //verify the config file
7. env LDAP_HOSTS=”<LDAP IP>” /usr/local/lib/mavis/mavis_tacplus_ldap.pl
//insert IP of LDAP server
8. vi resolve.conf
a. add this line to the file:
nameserver <ip of AD>
Add AD to hosts file to enable LDAPS
1. vi /etc/hosts
2. add <IP Address> <Full Domain Name>
Example:
127.0.0.1 localhost localhost.localdomain localhost4 localhost4.localdomain4
::1 localhost localhost.localdomain localhost6 localhost6.localdomain6
10.10.10.10. xxxxx.xxxx.local
3. wq
id = spawnd {
listen = { port = 49 }
spawn = {
instances min = 1
instances max = 10
}
background = yes
}
id = tac_plus {
access log = /var/log/tac_plus/access/%Y%m%d.log
accounting log = /var/log/tac_plus/acct/%Y%m%d.log
mavis module = external {
script out = {
# Require group membership:
if (undef($TACMEMBER) && $RESULT == ACK) set $RESULT = NAK
# Don.t cache passwords:
if ($RESULT == ACK) set $PASSWORD_ONESHOT = 1
}
setenv LDAP_SERVER_TYPE = “microsoft”
setenv LDAP_HOSTS = “ldaps://<AD domain>:636” #Insert domain name of AD server
setenv LDAP_SCOPE = sub
setenv LDAP_BASE = “dc=lab,dc=local”
setenv LDAP_FILTER = “(&(objectclass=user)(sAMAccountName=%s))”
setenv LDAP_USER = “XXXXXX@xxxxx.local” # <AD Admin name>@<Domain>
setenv LDAP_PASSWD = “XXXXXXXX” #AD Password
setenv REQUIRE_TACACS_GROUP_PREFIX = 1
exec = /usr/local/lib/mavis/mavis_tacplus_ldap.pl
}
login backend = mavis
user backend = mavis
pap backend = mavis
host = labswitch4 { #Defines host or group of hosts
address = ::/0 #insert address for specific host or ::/0 for all
prompt = ”
————-
W A R N I N G
————-
Unauthorized access prohibited
Authorized access only
This system is the property of Tenable Network Security.
Disconnect IMMEDIATELY if you are not an authorized user!
Contact ITS for help.\n ”
failed authentication banner = ”
———————————————————
NOTICE
%M%D-%%c-%%C-%%u
Failed authentication will be logged and reported
———————————————————”
enable 15 = clear <some password> #global enable Password
key = <some key> #host tacacs key
}
group = admin {
enable = login
default service = permit
message =”\n You are logged in with Admin Privs\n”
service = shell {
default command = permit
default attribute = permit
set priv-lvl = 15
}
}
group = servicedesk {
enable = login
message = “\n You are logged in with Service Desk Privs\n”
service = shell {
cmd = enable {permit “.*”}
cmd = show {
permit “running-config .*”
permit “ip .*”
permit “version .*”
deny “.*”
message deny = ”
*************************************************************
*You do not have the privilege level to execute this command*
*************************************************************
”
}
}
}
group = serv {
message = “\n You are logged in with Server Group Privs\n”
enable = login
service = shell {
cmd = enable {permit “.*”}
cmd = show {
permit “running-config .*”
permit “ip .*”
permit “version .*”
deny “.*”
message deny = ”
*************************************************************
*You do not have the privilege level to execute this command*
*************************************************************
”
}
}
}
group = security {
message = “\n You are logged in with Security Group Privs\n”
enable = login
service = shell {
cmd = enable {permit “.*”}
cmd = show {
permit “running-config .*”
permit “ip .*”
permit “version .*”
deny “.*”
message deny = ”
*************************************************************
*You do not have the privilege level to execute this command*
*************************************************************
”
}
}
}
}
Cisco AAA configuration
aaa new-model
!
!
aaa authentication login CONSOLE local
aaa authentication login TACSERV group tacacs+
aaa authentication enable default group tacacs+
aaa authorization config-commands
aaa authorization exec TACSERV group tacacs+ if-authenticated
aaa authorization commands 0 TACSERV group tacacs+
aaa authorization commands 1 TACSERV group tacacs+
aaa authorization commands 15 TACSERV group tacacs+ if-authenticated
aaa authorization configuration TACSERV group tacacs+
!
!
!
aaa session-id common
line con 0
login authentication CONSOLE
line vty 0 4
authorization commands 0 TACSERV
authorization commands 1 TACSERV
authorization commands 15 TACSERV
authorization exec TACSERV
login authentication TACSERV
transport input ssh
Setting up Active Directory Security Groups
1. Create 4 security groups in Active Directory named:
a. tacacsadmin
b. tacacssecurity
c. tacacsserv
d. tacacsservicedesk
NOTE: Tac_Plus truncates the TACACS portion of the above groups. The tacacs portion is used as an identifier.
2. Assign users to each security group to give them access to a restricted set of commands
Starting and Stopping the server
NOTE: Every time a change must be made to the configuration (tac_plus.cfg) script located in /usr/local/etc the server must be restarted for changes to take effect.
1. Starting the server
a. /etc/init.d/tac_plus start
2. Stopping the server
a. /etc/init.d/tac_plus stop
3. Restarting the server
a. /etc/init.d/tac_plus restart
Troubleshooting
1. LINUX: Netstat –lp | grep tac //verify that TACACS is listening on port 49
2. LINUX: Tcpdump –nn port 49 //view authentication or authorization traffic
3. LINUX: /usr/local/bin/mavistest –d -1 /usr/local/etc/tac_plus.cfg tac_plus TAC_PLUS <USERNAME> <PASSWORD>
Ex./usr/local/bin/mavistest –d -1 /usr/local/etc/tac_plus.cfg tac_plus TAC_PLUS jsmith passW0rd
NOTE: Will return output displaying active directory queries.
4. CISCO: debug aaa authentication //displays the aaa authentication attempts and successes
5. CISCO: debug aaa authorization //displays the aaa authorization attempts and successes
Cisco AAA configuration
aaa new-model
!
!
aaa authentication login CONSOLE local
aaa authentication login TACSERV group tacacs+
aaa authentication enable default group tacacs+
aaa authorization config-commands
aaa authorization exec TACSERV group tacacs+ if-authenticated
aaa authorization commands 0 TACSERV group tacacs+
aaa authorization commands 1 TACSERV group tacacs+
aaa authorization commands 15 TACSERV group tacacs+ if-authenticated
aaa authorization configuration TACSERV group tacacs+
!
!
!
aaa session-id common
line con 0
login authentication CONSOLE
line vty 0 4
authorization commands 0 TACSERV
authorization commands 1 TACSERV
authorization commands 15 TACSERV
authorization exec TACSERV
login authentication TACSERV
transport input ssh
Setting up Active Directory Security Groupsa
NOTE: Make sure that Certificate Services is installed if using Ldaps.
1. Create 4 security groups in Active Directory named:
a. tacacsadmin
b. tacacssecurity
c. tacacsserv
d. tacacsservicedesk
NOTE: Tac_Plus truncates the TACACS portion of the above groups. The tacacs portion is used as an identifier.
2. Assign users to each security group to give them access to a restricted set of commands
Starting and Stopping the server
NOTE: Every time a change must be made to the configuration (tac_plus.cfg) script located in /usr/local/etc the server must be restarted for changes to take effect.
1. Starting the server
a. /etc/init.d/tac_plus start
2. Stopping the server
a. /etc/init.d/tac_plus stop
3. Restarting the server
a. /etc/init.d/tac_plus restart
Troubleshooting
1. LINUX: Netstat –lp | grep tac //verify that TACACS is listening on port 49
2. LINUX: Tcpdump –nn port 49 //view authentication or authorization traffic
3. LINUX: /usr/local/bin/mavistest –d -1 /usr/local/etc/tac_plus.cfg tac_plus TAC_PLUS <USERNAME> <PASSWORD>
Ex./usr/local/bin/mavistest –d -1 /usr/local/etc/tac_plus.cfg tac_plus TAC_PLUS jsmith passW0rd
NOTE: Will return output displaying active directory queries.
4. CISCO: debug aaa authentication //displays the aaa authentication attempts and successes
5. CISCO: debug aaa authorization //displays the aaa authorization attempts and successes
A Survey of Computer Interfaces for People with Disabilities
A Survey of Computer Interfaces for People with Disabilities
With the evolution of technology, this is a critical time for people with disabilities who have much to gain by accessing emerging technologies–and much to lose if access is denied.
(Atkinson et al, 2003, p. 177)
Computing interfaces that provide access to technology for people with disabilities is necessary more than ever. It is important that accessibility to the Internet, electronic educational sources, and computing power is available at both the home and workplace. The evolution of computing technology has provided for lower cost higher performing machines that can handle the real-time processing needed to provide better accessibility features.
The current unemployment rates for people without disabilities is 9.4% compared to 14.8% for those with disabilities (Monthly Labor Review, 2011). Although it cannot be directly attributed to accessibility, society must strive to provide everyone with a fair chance to succeed. Awareness of current available options and research will help provide a better idea to maximize accessibility for those with disabilities.
This paper was written with the intention to educate people of the current state of accessibility options available as well as the research currently taking place. Because of the vast amount of technologies and devices available only a select number of them will be discussed. The hope is to cover technologies that directly affect those with hearing disabilities, paralysis, blindness, and other visual impairments, cognitive, and learning disabilities, and amputation.
Problems in Computing for People with Disabilities
As a preface to the technologies that are available or are currently in research this section provides an overview of the limitations and barriers that accessibility technologies must help overcome. Although every technology will most likely only address one type of barrier it is important to fully understand what current problems these technologies are solving. “These barriers can be grouped into three functional categories: Barriers to providing computer input, interpreting output, and reading supporting documentation” (Burgstahler, 2001, p. 1).
Input barriers exist when a user is functionally unable to use directly conventional devices such as a keyboard or mouse. Such problems can be found in people with full or partial paralysis, blindness, amputation, and cognitive, or learning disabilities. Modern advances in technology have created hardware and software solutions to help overcome these barriers. Devices designed to replace the keyboard and mouse and software that creates a simple or bigger version of an interface are available solutions. Later in this paper an eye tracking system will be discussed that allows the user to use their eyes as a mouse on screen.
Output and the ability to read supporting documentation barriers exist when a user is unable acquire the visually stimuli that a computer system interface offers. Generally in this case the user cannot hear, has low vision, or blindness. Solutions to this problem do exist in both hardware and software forms. Special output devices called Braille displays, speech synthesizers, visual sounds, color contrast settings, and on-screen magnifiers are available to provide an alternative to the tradition monitor and speaker.
As technology continues to evolve so will the solutions to the barriers in universal accessibility. Computers are becoming an increasingly larger portion of society providing a better quality of life and education to everyone. The next section provides a closer look at modern human-computer interfaces that currently or will change the lives of those using them.
Operating System Accessibility Options
Advancements in software and hardware research greatly have increased the ability to include tools built directly into operating systems such as Microsoft Windows (www.microsoft.com/enable) and Mac OS X (www.apple.com/accessibility). Both of these operating systems have made an effort to include basic accessibility features that can be enabled from within the operating system. These features include image magnification, text-to-talk, on-screen keyboards, visual sounds, sticky keys, and Internet accessibility. (Atkinson et al, 2003, p. 177) Mac OS X has also included the ability to simplify the operating systems interface for those with cognitive and learning disabilities as well as the support for Braille displays that will be discussed later in this paper.
Both of these operating systems feature a variation of speech recognition software. Speech recognition software allows the user to say commands rather than use a mouse or keyboard. This powerful feature was at one time very hard to use and unreliable. Since then processing power has increased the technology has become far more accurate and easy to use. As a test speech recognition software was enabled using a Windows 7 machine. The speech recognition software performed exceptionally well for basic functionality commands which were printed during the setup. As an attempt to test the speech-to-text feature, the author used it for 90% of the this paragraph. Problems in translation did occur however it could be attributed to the lack of time to set up and train the software for the voice.
Alternative Keyboard Solutions
Alternative solutions to conventional keyboards provides users with different motor skill abilities to increase their accuracy and usability. Because certain situations require different features keyboard manufacturers have developed various version that increase the accessibility of individuals with disabilities. Figure 2 displays a summary of the most common types of alternative keyboard types available.
| Alternative Keyboard Types | |
| Mini Keyboards | A keyboard with miniature buttons. These keyboards are for users with fine motor skills that require a much smaller area to type. Could be used with mouth stick, pointer, or fingers |
| Expanded Keyboards | Generally consist of bigger buttons. Allows for a greater range of motion. Could be used with fist, feet, hands, or fingers. |
| Chording Keyboards | Consist of a fewer number of keys. Combinations of keys create characters. Often the most common characters are the initial keys. |
| Braille Keyboard | Keyboard with Braille characters where the normal alpha-numeric keys are. |
Figure 1, (Brodwin et al, 2004, p. 29)
Alternative Mouse Solutions
Alternative types of mice are much fewer than that of their keyboard counterpart. Whereas keyboard remain static during their use, the mouse is a dynamic device. The unpredictability of its movements have led to only a few physical adaption’s. Hands-free technology is increasingly becoming more of a topic of research. The next few sections of this paper will provide information on further in-depth hands free solutions for individuals who have severe motor skill impairments. Figure 2 provides a summary of the different types of mice available on the market that aid those with physical disabilities.
.
| Alternative Mouse Types | |
| Track Ball | Uses a ball that can be pivoted with one hand while the other hand hits a lock down button. Easy for highlighting, dragging, and dropping. |
| Mouse Sticks | Uses a pressure sensitive stick that allows the user to use one finger to control the mouse. |
| Hands-Free Mouse | Head tracking unit, Eye tracking system, or Brain Computer interface. |
| TrackPad | Found it most laptop computers. Area of movement is low and allows for clicking without button interaction. |
Figure 2, (Brodwin et al, 2004, p. 30)
Braille Displays and Text-to-Speech
Braille displays provide an alternative solution for those who suffer from blindness or have extremely low vision. Using a grid of holes with pins these machines incorporate motors that can create the Braille alphabet and numeric system. Braille displays are much like a Braille book however they display information as it is requested from the user. These devices can be used in popular operating systems and even with phones for texting via Bluetooth. Most Braille displays are expensive ranging from $1000 to $5000 devices, depending on the number of cells on the unit. Venders selling these types of displays can be easily found by doing a web search or checking out an online auction house.
Text-to-speech is an alternative to Braille displays and comes standard on most operating systems. This software uses a speech synthesizer to vocalize on-screen text and alerts so a user with a visual disability can interact with the system. Text-to-speech software works well in providing auditory feedback about the status of a system and reading contents of web pages. There are drawbacks to the system as it cannot access content embedded in graphical images unless the content is in an accessible format (Burgstahler et al, 2007, p. 94). Because this software comes standard on most operating systems the only cost is the operating system itself. Commercial versions available that have different features and voices.
Eye Tracking Systems
The use of eye tracking systems benefits those individuals who suffer from paralysis or other diseases or situations that decrease or eliminate movement of the body below the eyes. These tracking systems generally do not require substantial processing power to implement and are cost-effective solutions. Many of these eye tracking interfaces have been designed through universities however there are commercial vendors that specialize in eye tracking and its various benefits including sales analysis and car safety features.
Using a camera and computer software the system can be set up and used as a human-computer interface that allows a person to control an on screen mouse with eye movements. Research into the algorithms and technology to create affordable eye tracking solutions for people with disabilities has been conducted by a team from the National Central University in Taiwan. This research used a 533mhz Pentium II pc running Windows 2000 and a Sony CCD camera (Su et al, 2006, p. 319). In this study the CCD camera was used to detect a human face using a skin color filter method. Further detection of the eye was processed in real-time from the computer using advanced programming techniques. The team ran tests successfully that resulted in their subjects to navigate to areas on the screen. Since this study eye tracking software can be found on the Internet freely available and in open source format and usable with many web cams.
Current and future research expand upon the approach of eye tracking as an interface for people with disabilities, to a powerful research tool for various conditions such as Dyslexia and Attention Deficit Disorder. This research uses the specifically designed programs and an eye tracking interface to trace and record where the eye focuses on various words or images and for what length of time. The idea is that where a person looks is thought to be “on top of the stack” for cognitive processes (Poole & Ball, 2005, p. 3). Using this information of where attention is focused allows researchers to further gain an understanding of the human mind.
Future Research in Brain-Computer Technology
Brain-Computer Interface research is still in its early stages, however, is showing promising results for the future. Earlier research used large mainframe computers and non -invasive electrodes to read and process the information. These studies still relied on physical movement of the eye to generate electroencephalogram (EEG) that was computed in with minor lag to show results (Mcfarland & Wolpaw, 2011, p.60). Although there was still muscular involvement used this BCI was monumental.
Since then research has been conducted using real-time processing on modern computers. Development of home use systems has provided functionality by using an electrode cap, a laptop computer and a screen in front of the individual (Mcfarland & Wolpaw, 2011, p. 60). This functionality includes the ability to use letter selection to type on screen words onto a computer. In the May 2011, Communications of the ACM reported that a 49-year-old man who suffered from loss of motor functions because of advanced amyotrophic lateral sclerosis (ALS) has been using this device for three years and prefers it over the eye tracking system he had before.
The practical uses for extreme motor function loss are apparent and useful today however, BCI deserves much more research to take this technology to the next level. Other studies include the use of BCI to control wheelchairs, or prosthetic limbs. With this technology still in an early age, the promise of achievement is evident.
Future Research in Facial Mouse Technology
Chinese students at National Central University are developing a way of controlling an onscreen mouse using facial muscle activity patterns. The idea is to use electromyography, and a minimal amount of electrodes to translate muscular movement to onscreen movement. Much like the brain-controlled interface that was discussed in the previous section, noise is picked up by the electrodes and fed to a computer. The difference is the facial mouse uses EMG that is mostly considered noise to the BCI.
The students have developed a working model of which they tested on six human subjects. Each subject was given 12 commands to complete during the test. On average the test subjects scored above 83% in accuracy. This accuracy is also coupled by with five additional trials timing the seconds to complete 12 commands. The trial group successfully completed the commands in 35-59.2 seconds.
Summary
Computing technology continues to grow, increasing societies quality of life. Education, information, and entertainment are readily available for anyone that has access to the Internet. As the availability of computers has increased so should the accessibility options. Enabling accessibility to people with various disabilities opens new possibilities that will positively affect society.
This paper was written with the intent to inform people of the issues, solutions, and research that are affecting those people who cannot use conventional user interfaces for computing. In the near future it is hoped that the research is properly funded so it will ignite a spark of genius in those who beforehand were not given the proper tools to participate in technologies evolution. People should be given an opportunity to succeed, and this is no different with computing technology. It is societies duty to continue research that will benefit those who cannot use conventional computer access.
References
Atkinson, T., Neal, J., & Grechus, M. (2003). What Works for Me: Microsoft Windows XP Accessibility Features. Intervention in School and Clinic, 38(3), 177-80.
Brodwin, M. G., Star, T., & Cardoso, E. (2004). Computer Assistive Technology for People who Have Disabilities: Computer Adaptations and Modifications. Journal of Rehabilitation, 70(3), 28-33.
Burgstahler, S. (2001). Working together: people with learning disabilities and computer technology. Exceptional Parent, 31(6), 36-39.
Burgstahler, S. E., & Ladner, R. E. (2007). Increasing the Participation of People with Disabilities in Computing Fields. Computer, 40(5), 94-97.
Cheng-Ning, H., Chun-Han, C., & Hung-Yuan, C. (2006). Application of facial electromyography in computer mouse access for people with disabilities. Disability & Rehabilitation, 28(4), 231-237.
Mcfarland, D., & Wolpaw, J., (2011). Brain-computer Interfaces for Communication and Control. Communications of the ACM, 54(5), 60-66
People with disabilities and employment. (2011). Monthly Labor Review, 134(6), 2.
Poole, A., & Ball, L. (2005). Eye Tracking in Human-Computer Interaction and Usability Research. Current Status and Future Prospects. Human Computer Interaction Lancaster University, UK
Su, M., Wang, K., & Chen, G. (2006). An Eye Tracking System and its Application in Aids for People with Severe Disabilities. Biomedical Engineering Applications, basis & Communications, Vol. 18 No. 6, pp. 319-327
Web Mining
I.INTRODUCTION
The Internet is expanding at an exponential rate. More individuals are logging on each day with the decrease of the digital divide. Business and consumer entities alike are both experiencing the overwhelming phenomena of information overload. [Pierrakos, 2010] E-Commerce is growing as more consumers choose the World Wide Web as their new shopping medium. The need to discover knowledge from and make sense of this information is needed to maximize company profit and customize what information is delivered to whom.
Basic techniques for information discovery on the user end consist of web directories such as Yahoo (www.yahoo.com), Google (directory.google.com), or ODP (www.dmoz.org). This form of information discovery requires human interaction to maintain a list of web sites on information pertaining to the user’s needs. Other types of user end information discovery methods are search engines such as Google (www.google.com) and Microsoft’s Bing (www.Bing.com). These types of information discovery require the user to consciously search for content pertaining to their area of interest. Recently new advancements in web mining technology have paved the way for advanced advertising programs and suggestive search. Each of these two new technologies utilizes preferences from past user activity or profiles built by the user.
This paper gives a general overview of web mining as well as providing further information on its three categories. This type of knowledge discovery has been a major attraction for the corporate and marketing world. The goal of this type of research is to provide information on user preferences and activities and derive knowledge from that information to effectively deliver content through personalization. This type of research has been a major attraction with E-Commerce.
This paper is a literature review of several papers dealing with the general topic of web mining. It also consists of literature research findings of the three categories of web mining in order to provide a more in depth understanding of the topic as a whole. Table 1 provides a categorized format displaying the key literature findings highlighted in this paper, by topic and author for quick reference to the materials. The selected references were found from various literary research mediums such as IEEE Xplore, EBSCOhost, CiteSeerX, and Google Scholar. A few additional sources were found from a generational research method.
| Table 1: Literature Findings by Category | ||
| Web Structure Mining | Web Usage Mining | Web Content Mining |
| Kolari and Joshi, 2004 | Nina., et al., 2009 | Nair, 2009 |
| Pierrakos, 2010 | Pol., et al., 2008 | |
The rest of this paper is structured as follows. Section two provides a generalized overview of web mining and progresses into the three main categories in further detail. Section three is dedicated to the potential of future research that could be conducted in the field. Finally section four concludes the paper.
II. Web Mining
Web mining is the set of techniques of Data Mining applied to extract useful knowledge and implicit information from web data. [Nina et al., 2009] This type of research has been an attraction of corporate entities as well as consumers interested in its rising privacy concerns (discussed in section six), because of the type of information it provides. Exponential increases in the information made available by the Internet, has made research on web mining a necessity.
Current and past research on the topic of web mining can be broken down into three categorical types;
I. Web Structure Mining
II. Web Content Mining
III. Web Usage Mining
These categories each require their own specific techniques in order to extract and make sense of information. Each category will be discussed in detail in the following sections. It is important to understand that the categories of web mining often overlap depending on what the implementer wishes to mine.
Since the internet is filled with structured, semi-structured, and unstructured data. This lack of scheme for information provides a daunting task when trying to extract useful information. Technologies such as database, information retrieval and artificial intelligence, machine learning and natural language processing, network analysis and information integration are needed in order to make sense of chaos. [Nair, 2009]
| Table 2: Structured, Unstructured, and Semi-Structured data | |
| Structured Data | Data that is found in a table, list or tree. This type of data is common in product or price lists. |
| Semi-Structured Data | Data that is found in a web page. Contains various syntaxes such as HTML. |
| Unstructured Data | This type of data is commonly a text document, or multimedia file such as images, videos, or audio files. |
The following sections are breakdowns of web usage mining, web structure mining, and web content mining.
Web Usage Mining
Web usage mining is a discovery method used to derive information about the users. This category of web mining provides useful information about the users behaviors and usage pattern. Understanding the users behavior has become of increasing interest to E-Commerce companies. The ability to use this technology to extract information about what the user prefers has paved the way to a new form of marketing and personalization in the web experience. Keeping track of various information regarding the user’s interaction with the web, in general or that of a more specific site has allowed companies to profile the user’s likes and dislikes and direct content toward those preferences. This opens up the ability to direct marketing campaigns appropriately towards those who are more receptive therefore increasing the probability of a sale or selection to use a service.
Web usage mining has attracted a plethora of researchers who have found a great deal of interest in dissecting the internet activity of users. This category alone has a vast amount of information available on every technical aspect. The scope of this paper however will remain a basic view in order to provide a general understanding rather than an in depth technical understanding of the topic.
In the paper entitled “Pattern Discovery of Web Usage Mining” by Nina, et al (2009), retrieving information as well as processing it into a final product is made clear. In order to obtain the usage information there are three main sources; Web Servers, Proxy Servers, and Client Servers. [Nina et al., 2009] Each source provides valuable information in which can provide knowledge of internet activity. On the server side, web servers provide detailed logs which often include the IP, date and time of the request. Proxy Servers generally contain the same information as the web server however in addition they contain all of the connections made in a more global scale. The Client side can consist of applications, often known as spyware or modified browsers, such as Google Chrome which tracks information and send it back.
Once the initial data is collected it must undergo three phases in order to become understandable information. These phases are:
I. Data Preparation
II. Pattern Discovering
III. Pattern Analysis and Visualization
[Nina et al., 2009] Each of these phases uses specific algorithms in order to clean the data, find specific patterns within the data and present the data in a readable view. Often graphs are utilized to show general information as well as specific information that may even include geographical representation from site visitors.
The papers researched provided a general understanding for the need of web usage mining. They also provide a pseudo understanding of the steps needed of transforming this type of log file information to useful information that essentially aids in making proper decisions. These decisions can include web design that maximizes the user’s interaction with the web page, as well as the ability to implement personalization features to attract specific groups. After much review it would be helpful for research to be conducted in real time web mining in order to provide up to the minute monitoring of web usage. This research could potentially increase the ability to combat the dynamically changing habits of the website user. It would also be able to log trends and compare to logs of other days much like that of sales projection services found in Point of Service systems.
Web Content Mining
The web is a constant growing medium for accessing a variety of information stored in different parts of the world. (Pol., et al, 2008) Information such as images, music, video and text are available almost everywhere. Web content mining is a category of web mining that tries to extract information from the web page itself. This type of web mining however is not as easy as the previous technique of web usage mining. Unlike web usage mining which focuses on server logs or information gathering programs, web content mining focuses on the vast amount of web pages found on the web. This presents various problems. The paper by Liu and Chang presents issues and discusses the current technology used to achieve web content mining. A summary of the various issues can be found in Table 3.
| Table 3: Issues in Web Content Mining | ||
| Redundant information displayed in various syntaxes | The Web is dynamic and always changing | The Web is a virtual society containing interactions between people, or automated systems |
| Data exists of all types including multimedia data, tables and texts | Various types of information can be found on a page including advertisements, navigation panels, etc. | Many web pages provide services that contain input parameters |
| The Web consists of a majority of Semi-structured information due to HTML | The amount of the information is huge and continues to grow | Topics of information are limitless, wide and diverse |
[Liu and Chang, 2004]
The most common form of web content mining, deals with various structured data types. (see table 2 for definition) These data types include product lists, services, prices or other types of information that can be used to incorporate value added services such as comparative shopping or provide keys for meta-search. [Liu and Chang, 2004] Liu and Chang explain that there are three technologies currently used in order to extract structured data. These methods from the most labor intensive to the least include;
I. Manually written extraction program
II. Wrapper induction or learning
III. Using an automated system such as MDR or RoadRunner
Extracting text from a physical web site requires much more than extracting information from a structured source. Current research in this type of data extraction is closely related to the research in text mining, Natural Language processing, and information retrieval. Other research includes finding common language patterns as well as question-answering methods. Extracting unstructured or semi-structured text faces many of the challenges found in table 3. Specifically Liu and Chang address the concept of noise. Noise can be defined as those areas on the web page that cause a redundancy, such as navigational bars and advertisements. Filtering this type of information from the web page is necessary in order to extract the core data.
After researching the topic it is clear making sense of web content itself is an extremely daunting task. However the benefits of doing so can be found all over today’s web. An example that consumers use every day would be price comparisons of various services or items in order to match up several companies at once. Liu and Chang also bring up the importance of this technology when used to mine opinions from consumers. This type of mining utilizes various reputable web sites containing forums or other types of reviews in order to develop a clear picture of an organization’s success. This information is used in marketing research to develop reports and analyze word of mouth which is extremely important for any company’s success.
Web Structure Mining
Web structure mining provides a ranking or authoritativeness which enhances search results though filtering derived from the web’s hyperlink structure. [Kolari and Joshi, 2004] Unlike web content mining which uses the pages content, web structure mining derives information from the way pages are linked from its links. They type of web mining uses a method which clusters sites linked together to one another and those sites link to it. This creates a web of sites which generally have a similar topic or purpose.
Web structure mining is often combined with web content mining in order to provide a new level of precision. This technology is of great interest to web based search engines which utilizes it in order to provide a greater amount of accuracy. Extracting direction of web links web structure mining provides knowledge on what sites are authoritative from the links from various hubs to the source. This helps provide page rankings to the web sites with the highest amount of links to them. Generally this type of ranking provides the web site with the most information.
In a paper by Kolari and Joshi technology being used for web structure mining is explained. These technologies include the PageRank system which is utilized by Google’s search engine, The Clever system, and an additional approach which utilizes web communities. Each of these approaches uses the web structure mining category in order to rank pages in order to determine the most authoritative web sites in that community.
The first technology being discussed is the PageRank system. This system is utilized by Google in order to populated their results with the most relevant web sites first. PageRank uses a crawler which pre-computes search results before they are returned. [Kolari and Joshi, 2004] The crawler then returns the information about the ranking of the page which includes various aspects including popularity and what pertains to this section the number of links leading back to the page itself. This is used to determine if a user will generally stay at this page or go off to another page to find out more information.
The second technology is the Clever system. This system incorporates not only web structure mining, but web content mining. The system utilizes the query term and compares it to text in or near the anchor text in the HTML page. [Kolari and Joshi, 2004] This system does not only utilize the links to other sites or to the site itself to gain rank but also the sites genre compared to the query. This provides a higher level of accuracy.
The third technology or method is to develop an idea of web communities. Web communities are web sites, often similar in interest, which are linked to each other. Kolari and Joshi describe web communities as web rings. This term was coined because they are essentially connected in a big circle. When mining a web community those interlinking website are analyzed to find sites that simply don’t link back. These types of sites are then considered the community core or the authoritative web site.
All three of these methods of web structure mining provide results based on the pages authoritative value. Each of these techniques are valid and provide a high level of accuracy when trying to find the most relevant information.
III. Future Research
Constant change in markets requires the quick adaption of a business in order to compete in the free-market world. Being the best requires research in order to find what a consumer’s wants, needs and dislikes are. With the internet and its vast amount of users growing it is necessary for web mining research to be conducted. Customer relations, sales and marketing departments should utilize the current web mining techniques in order to gain a fuller perspective of the customer.
Future research in this field should be conducted in both web content mining and web usage mining. Not only is it important to gain knowledge of a consumers internet usage but it is important to find out what their opinions are. Research utilizing both content and usage mining would be beneficial for the industry in order to paint a complete picture of the consumer.
Traditional consumer research was done with a questionnaire or survey. This type of research creates a very limited selection of opinions which narrows or distorts the actuality of the research. Using new web mining and artificial intelligence techniques it could be possible to sample a much broader range of customer opinions from existing forums and not just a selected few sites.
Combining research of these forums with an analysis of consumer browsing behavior would provide a remarkable tool for business customer relations, sales, and marketing. This type of software incorporated with various decision support systems would allow for far more current information to be made readily available for upper management to formulate plans and campaigns.
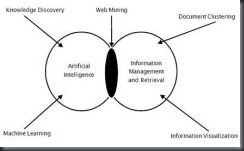
Figure 1: Areas in Web Mining. [Nair, 2009]
The internet and web mining are still in their infancy. Technologies needed in order to advance web mining must also be researched as well. Figure 1 shows how web mining is dependent on other technologies in order to evolve. Research in these other technologies will aid in web mining becoming a major source of information used to make decisions.
IV. Conclusion
In this paper a generalized overview of web mining was discussed as well as some of the new research that has been done. Web mining was broken down and analyzed into its three major categories of study. Specific research papers were organized per section and discussed according to their topic. Each of these research papers introduced a new aspect of web mining furthering the general knowledge of the topic.
As technology grows so will the internet and the web. Internet based business as well as those not based on the internet all will find their companies researching this vast landscape of knowledge in order to get ahead of the competition. The topic of web mining discussed in this paper will continue to be a great interest in those companies trying to get an advantage.
Abilities to increase personalization when browsing, to optimize web site development for maximum usage, to find information faster, and to find links between vast amounts of web sites
are just a few of the advantages of web mining. Today, more than ever we see companies marketing products to those who are going to buy. Web sites are optimized with link patterns to get the most exposure from each visitor. Each of these examples is of a direct result of web mining.
As more and more research is done in all of web mining’s supporting fields so will the power of web mining. Section three gives the reader an idea of where this research may end up in the future. As this field becomes more and more attractive to the business world more research will be done. The future of web mining will be a future filled with powerful research tools that will become standard for any business.
References:
Xiaohua, H., Cercone, N. (2004). “A data warehouse/online analytic processing framework for web usage mining and business intelligence reporting.” International Journal of Intelligent Systems, 19(7), 585-606.
Weihui, D., Xingyun, D., & Tao, S. (2009). “A Smart Targeting System for Online Advertising.” Journal of Computers, 4(8), 778-786.
Nair, N. (2009). “Mining the Web for Managing Web Content.” IUP Journal of Systems Management, 7(3), 7-16.
Zhang, Q., Segall, R. (2008). “WEB MINING:: A SURVEY OF CURRENT RESEARCH, TECHNIQUES, AND SOFTWARE.” International Journal of Information Technology & Decision Making, 7(4), 683-720.
Nina, S.P., Rahman, M., Bhuiyan, K.I., Ahmed, K. (2009) “Pattern Discovery of Web Usage Mining,” Computer Technology and Development ICCTD ’09. vol.1, no., pp.499-503, 13-15
Nasraoui, O., (2009). “A Web Usage Mining Framework for Mining Evolving User Profiles in Dynamic Web Sites.” IEEE Transactions on Knowledge and Data Engineering, Vol. 20, 2
Kosala, R., Blockeel, H. (2000). “Web Mining research: A Survey”, SIGKDD Explore 2
Tyagi, N., Solanki, A., & Wadhwa, M. (2010). “Analysis of Server Log by Web Usage Mining
for Website Improvement.” International Journal of Computer Science Issues (IJCSI), 7(4), 17-21.
Qiu, L., Li, Y., & Wu, X. (2008). “Protecting business intelligence and customer privacy while
outsourcing data mining tasks.” Knowledge & Information Systems, 17(1), 99-120. doi:10.1007/
s10115-007-0113-3.
Pierrakos, D., (2010). “Personalizing Web Directories with the Aid of Web Usage Data.” IEEE Transactions on Knowledge and Data Engineering, Vol.22, 9
Liu. B., Grossman, R., & Zhai. Y., (2004). “Mining Web Pages for Data Records.” University of Illinois at Chicago, Published by IEEE
Pol, K., Patil, N., Patankar, S., Das, C., (2008). “A Survey on Web Content Mining and Extraction of Structured and Semistructured Data,” Emerging Trends in Engineering and Technology, 2008. ICETET ’08. pp.543-546, 16-18
Kao, H., Lin, S., Ho, J., Chen, M., (2004). “Mining Web informative structures and contents based on entropy analysis,” Knowledge and Data Engineering, IEEE Transactions on , vol.16, no.1, pp. 41- 55
Liu, B., Chang, K., (2004). “Explorations, special issue on Web
content mining” SIGKDD, vol. 6, no. 2, pp. 1-4,
Kolari, P.; Joshi, A.; , “Web mining: research and practice,” Computing in Science & Engineering , vol.06, no.4, pp. 49- 53, July-Aug. 2004
Small Wireless Networks and their Vulnerabilities
Small Wireless Networks and their Vulnerabilities
Wireless networking quickly has been adopted by homes and business after its introduction. These 802.11x networks have provided cable free access to privately owned networks and the Internet. This form of networking is extremely cost-effective and easy to set up for the not-so-technical individual. Both home and small business network access points are easily found in any major department store for usually less than $100. Higher end models such as those developed from Cisco come with many more features for the networking engineer wishing to implement them into a project. However, along with these features comes a much higher price. This paper mainly focuses on non-professionally installed Wireless networks.
“The potential presence of 10 billion such devices over the next decade [introduces serious questions of security.] ” (Osorio, 2008, p. 92) New security protocols have been developed to protect the traffic of a network as well as maintain access only to those authorized. These protocols have displayed both vulnerability and security when implemented into wireless networks. Another major issue in the security of wireless networks is the human factor. Often lack of technical knowledge or ignorance to potential threats plays a role in the nonexistent or poor network security measure employed.
Legal Cases of Wireless Network Intrusion
Protection against network intrusion in a home and business environment is a necessary step to avoid potential personal loss of digital property, direct monitoring of activity and network abuse by those connecting without permission (US-CERT, 2006). Most unsecure networks will simply be used for leaching Internet and other harmless activities. However, a malicious user successfully connected to a unsecure wireless access point could utilize this connection to further carry out attacks anonymously under the cover of the parent network.
In 2004, a California man was arrested for the malicious intrusion of several unsecured networks to send commercial adult electronic email advertisements. Nicholas Tombros of Hollywood, California used email addresses he obtained from a previous employer to orchestrate his mass spam attack. Even though Tombros was Operating under the cover of other people’s networks he was eventually traced back due to his affiliation with the site he promoted. (Slay & Turnbull, 2005)
Another case of malicious intent involved two men named Adam Botbyl and Brian Salcedo in 2004 who utilized a unsecured access point to infiltrate Lowes corporate data center. The two men were convicted of accessing consumer credit information from the Lowes home improvement store chain and sentences to several years in a federal correctional facility. (Sipior & Ward, 2007) These men utilized a network weakness which, not only caused potential monetary loss, but also affected the reputation of the company.
Wireless Network Security Protocols
Wireless network security protocols were designed to provide a way for the owner of a wireless access point to ensure that the use of the network is theirs or those they permit only. To avoid unauthorized users from maliciously using a wireless network it is necessary to utilize at least one of the network security protocols below. Although there has been research conducted to compromise these security protocols utilizing any of them is better than no security at all.
Below are the basic features of each of the popular protocols found on most of today’s wireless access points.
| Security Protocol | Acronym | How it works |
| Wired Equivalent Privacy | WEP | Uses less advanced algorithms that can be decrypted using tools available on the Internet. |
| Wi-Fi Protected Access | WPA | Contains many security improvements over WEP. Utilizes key hierarchy that protects the existence of the WPA main Key. |
| Wi-Fi Protected Access 2 | WPA2 | Contains all WPA features plus Advanced Encryption Standard (AES). This new encryption standard is far more advanced than previously used RC4 encryption. |
Security Risks and Benefits of Network Monitoring Tools
Modern home and small business routers and commercial access points could utilize the security protocols discussed in the previous section. Although these routers and access points provide the option to employ security measures often these measures are dismissed by the people installing the hardware. The human factor or wetware aspect of this installation process provide an abundance of security risks to the owner(s) of the hardware and network.
Wireless networks are easily able to be detected utilizing network monitoring tools freely available on the Internet. These network tools come in either the form of simple point and click or full powerful command-line-driven software packages. Combined with the necessary network card that allows monitor (promiscuous) mode any person with a laptop can perform a War Driving session (described in the next section).
Although these tools appear to be made with hostile intent, and if used for such can provide serious network risk, they are often used for honest network monitoring applications and vulnerability assessments. “The difference between wireless hacking and wireless monitoring is intent and moral orientation” (Berghel, 2004, p. 25). Utilizing these tools for network discovery purposes have several benefits for those wishing to increase network performance as well as assessing their own network vulnerability. These benefits include the ability to view other local access points channels to make the necessary adjustments to avoid channel overlapping to increase network performance. Another key benefit is to see what networks are freely broadcasting their Service Set Identifier (SSID) and the type of encryption being used. This information can be valuable to a network administrator or a home user wishing to secure his or her network(s) from possible intrusion.
War Driving
In 1983 the movie WarGames starring Matthew Broderick as David, a young boy who had a love for video games utilized a program to dial up all the numbers in his home town of Sunnydale, California in search of a open modem connection. During the execution of David’s war dialing program he happened to stumble across a NORAD open line that connects him to a super-computer that controls the nuclear arsenal of the United States government. Although this was just a movie the applications of war dialing as a viable way to find open connections to networks have been proven throughout the years. Evolution of wireless technology has created a much easier and faster way of being able to discover open network connections that more than often lead to a gateway to the internet.
Today’s world of wireless access points both in home and business have led to a new form of war dialing to emerge called War Driving. Although different in technical aspects the concept of this form of network discovery remains. Similar to War Dialing that capitalizes on dial up network connections, War Driving capitalizes on those networks connected to a wireless access point.
Exploitation of Network Vulnerabilities
In this section of the paper the focus of network vulnerabilities of wireless networks is met with research using several tools to provide a clear understanding of the network security flaws found in a majority of access points monitored. The penetration test was on a wireless router using WEP protocol security was performed in a home test environment with the consent of the owner. As a preface to this test a War Driving session was performed with a network monitoring program. This program in no way attempted to connect to any networks to gain unauthorized access. This War Driving session had the sole intention to collect information on the network security used.
Results of War Driving Test
The test utilized a netbook with the Ubuntu 11.04 operating system installed running the Aircrack-ng (www.aircrack-ng.org) monitoring function Airodump-ng. The hardware utilized with the netbook was a Linksys Compact Wireless-G USB adapter that was purchased from Ebay for $13. Airodump-ng was set to write an output in the form of a CSV file in order to further analyze the results.
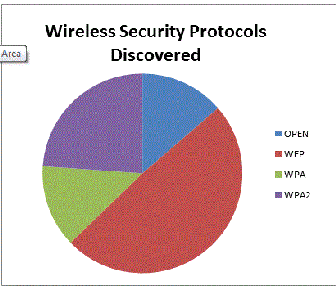 Figure 1, Wireless Security Protocols Analyzied during the War Driving session Figure 1, Wireless Security Protocols Analyzied during the War Driving session |
The location of this test was a radius of two miles that was selected do to the population of apartment buildings and the high likely hood of creating a larger sample size. A total of 352 total access points were recorded during a 45 minute run. Airodump-ng was configured to monitor all Wi-Fi channels in order not to focus on one specific popular channel. This approach led to a broader range of access points of both business and home hardware that may have been over looked during the process. Although other protocols than WEP, WPA, and WPA2 exist only these security protocols were assessed in the War Driving session.
The results of the War Driving session were unquestionably stunning. Of the 352 total access points monitored 48 were unsecured completely. (Figure 1) This represents approximately 14% of the overall access points assessed. The total amount of unsecured known business Wi-Fi connections collected during this session neared 21% of those 48 monitored.1
1Due to the scope of this test it is unclear how many of this 21% are vulnerable to attacks as very few may be unsecured Wi-Fi for public use and may not be connected to a valuable computing network source.
Wired Equivalent Privacy (WEP) was the next concern of this War Driving Session. During the 45 minute run an inexcusable 49% of all access points still used the WEP security protocol for security against outside attacks. Of these access points only 1% were businesses. Ironically that 1% consists of a local computer company that deals in Point of Service systems specializing in RFID and wireless tracking technology.
Wi-Fi Protected Access (WPA) and Wi-Fi Protected Access 2 (WPA2) comprised of 37% of overall network security protocols utilized in the War Driving session. Broken down WPA was 17% and WPA2 24%. Although these network protocols are able to be compromised, the amount of time and effort to do so negates the risk. It is plausible that a brute force attack could be utilized to gain access to this type of Wi-Fi connection however availability of other networks with little to no security would surely steer those with malicious ambitions away. Unless the intent is to attack such a network this security protocol is found as being the safest and most secure way of managing a wireless network.
Results of Penetration Test on WEP Network
The statistics in (Figure 1) have displayed that not only is 14% of the access points were readily available for an attack but 49% of the access points assessed were utilizing poor security or WEP. Known vulnerabilities have rendered WEP useless in the wireless protection realm. These vulnerabilities have rendered 63% of all networks surveyed as potential targets for malicious attacks or intrusion. Below the steps to crack a 64 bit web password are briefly discussed. The results are displayed in figure 2.
For this test a desktop computer running a virtual machine with Backtrack 5 Linux distribution (www.backtrack-linux.org) loaded is using the Linksys Compact Wireless-G USB adapter in monitor mode. Backtrack 5 comes pre-installed with many useful penetration testing software packages however, for this test the focus is on Aircrack-ng (www.aircrack-ng.org). Below is a summary of the necessary steps used in this type of attack. Notice that no command line functions are given however they can be easily found on the Internet with a simple search. (see Singh et al, 2010, for further information)
1. If this were a malicious attack the attacker would change their MAC address using a tool, included in Backtrack Studio 5, called MACCHANGER. Because this was in a test environment this step was skipped.
2. This step is the discovery phase that requires using the airmon-ng tool to discover MAC address of access points within range. Other useful information is given such as the ESSID, speed, encryption, and channel.
3. Once the targets necessary information is collected, it is necessary to monitor the packets coming from and to the access point. This is done using airodump-ng which allows the attacker to capture and record activity into a file, which will then be used by the aircrack-ng program.
4. Since all packet information is being collected it’s time to speed up the process using a aireplay-ng. This creates network traffic which speeds up the packet collection process.
5. Finally the file created to collect packets is piped into aircrack-ng. This software examines the collected packets and decrypts the WEP key
After successfully doing this crack 4 consecutive times the average time was approximately 14 minutes. If an attacker had the intent to break into this type of network they could achieve with speed and accuracy using the tools mentioned above. This test shows how vulnerable a wireless network is that uses poor security.
Summary
Wireless technologies will continue to grow due to its ease-of-use and cost-effective implementation. “The public is becoming accustomed to the mobility and ubiquitous internet access they provide” (Chenoweth et al., 2010, p. 134). As time goes by new security measures and protocols will be created and installed in wireless access points. Although these new security precautions will be available it is the responsibility of the human factor to implement them. The War Driving test in the previous section displayed that not only were more advanced security options not being used, but often no security at all was in place. General home and small office Wi-Fi network owner need to be educated in the uses of security on their access points.
References
Berghel, H. (2004). Wireless Infidelity I: War Driving. Communications of the ACM, 47(9), 21- 26..
Chenoweth, T., Minch, R., & Tabor, S. (2010). Wireless Insecurity: Examining User Security Behavior on Public Networks. Communications of the ACM, 53(2), 134-138.
Lashkari, A.H.; Danesh, M.M.S.; Samadi, B.(2009)A survey on wireless security protocols (WEP, WPA and WPA2/802.11i), Computer Science and Information Technology, 2009. ICCSIT 2009. 2nd IEEE International Conference, pp.48-52, doi:10.1109/ICCSIT.2009.5234856
Slay, J. J., & Turnbull, B. B. (2005). The 802.11 technology gap: case studies in crime. Retrieved from EBSCOhost.
Sipior, J. C., & Ward, B. T. (2007). Unintended Invitation: Organizational Wi-Fi use by external roaming users. Communications of the ACM, 50(8), 72-77.
Singh, A., Mishra, B., & Singh, S. (2010). WLAN Security Flaw: Cracking 64 bit WEP Key. International Journal of Computer Science Issues (IJCSI), 7(6), 296-299
United States Computer Emergency Response Team. (2006). Using Wireless Technology Securely. Retrieved June 19th, 2010, From http://www.us-cert.gov/reading_room/Wireless- Security.pdf